If you hand over your entire personal portfolio to a business to prove your identity, it’s only natural to wonder how that information is being handled.
And honestly, that’s fair. When someone makes a digital clone of your passport, the very least they can do is explain why and how they plan to protect it.
Customer data security is the core promise any responsible business should uphold.
There are strict rules and regulations to maintain it, but even with them, we’ve seen some examples of data breaches where sensitive KYC information was exposed.
Such incidents naturally raise questions about how transparent and safe the KYC process truly is.
In this article, you’ll learn everything you need to know about whether KYC verification is actually safe, what kind of risks it is susceptible to, and how to protect your data.
Βασικά συμπεράσματα
- KYC verification demands highly sensitive personal data, which makes airtight security non-negotiable
- Your identity information travels through vendors, auditors, and partners, and every handoff increases the risk of it being misused
- Responsible businesses fight back the risks of data compromise by introducing data encryption, strict access controls, legal compliance, and internal safeguards that actually annoy employees (as they should).
What Is KYC Verification Safety?

KYC (Know Your Customer) is the process for businesses to ensure their customers are real humans with real identities. And to do that, businesses need a pile of sensitive information.
KYC verification safety includes the measures meant to keep that information from becoming digital confetti in the hands of scammers.
These measures include encryption, secure databases, access controls, audit logs, etc.


Μην ανησυχείτε ποτέ ξανά για την απάτη με τεχνητή νοημοσύνη. TruthScan Μπορεί να σας βοηθήσει:
- Ανίχνευση AI που παράγεται εικόνες, κείμενο, φωνή και βίντεο.
- Αποφύγετε το σημαντική απάτη με βάση την τεχνητή νοημοσύνη.
- Προστατέψτε τα πιο ευαίσθητο περιουσιακά στοιχεία της επιχείρησης.
It is very, very important to keep KYC verification data safe. The data customers hand over for verification is exactly what cybercriminals are always on the lookout for!
It is high-value and really hard to change once stolen.
What “Safety” Means In The Context Of KYC Data Handling
The concept of data safety in KYC is pretty subjective.
If we’re being honest, no system is 100% impenetrable. In 2024, attackers stole millions of records from the KYC service World-Check, which is proof that big, well-resourced databases can also, sometimes, get compromised.
Of course, there are strict data-protection laws in place that govern how KYC information must be collected and stored. GDPR, CCPA, and PDPA are some of those examples.
So, a responsible business will always ensure the safety of its customers’ data collected during KYC.
But, as a customer, you do have your part to play in determining if the company you share your data with is trustworthy enough.
What KYC Verification Collects and Does
Any time you sign up for a bank account, a trading platform, a crypto exchange, or anything remotely financial, you must ensure you’re not a front for criminal activity.
And that requires you to send your personal data, which includes:
- Your full, legal name as it appears on your ID
- Date of birth
- Residential address
- Some form of government ID, i.e., passport, driver’s license, national ID card
- Biometric data
- Financial identifiers like a bank account or a credit card number
- Supporting documents, such as utility bills or tax statements, that validate your address
All this data is used to confirm that you have not previously been involved in any kind of suspicious financial activity.

What Happens After Submission
When you upload your personal documents, they get stored inside the company’s database. But besides that, your information also moves!
Many businesses use third-party KYC verification software that offers automated verification tools, like OCR scanners, biometrics software, fraud-detection engines, etc.
Some pieces of your KYC profile may also be sent to:
- Regulatory bodies
- Government agencies
- Financial partners
- Fraud analytics firms
Essentially, your data gets copied, backed-up, mirrored, and cached into several places.
Where the Real Risks Lie
Now, the security risks to your data are not just limited to the point when you initially upload it. The real concerns arise when your data travels.
The more systems your data passes through, the more exposure points there are.
A bank may have great security systems in place, but what about the verification vendor or the external auditor that holds a backup copy of it?
All it takes for your data to be compromised is one weak link.
As I mentioned earlier, many businesses outsource their KYC verification to external vendors, but those vendors themselves may be a potential breach point.
Sengzi, for example, is a KYC verification provider used by more than 600 financial institutions worldwide.
Just a few months ago, it reported a data breach in which more than 600 GB of sensitive customer verification data was reportedly put up for sale on the dark web.
Financial companies may also store your information long after you’ve stopped using their service.
The older the data and the longer it sits, the more likely it is to be caught in a system migration or server issue.
How Businesses Keep KYC Data Safe
Any business that genuinely cares about its customers knows that nothing destroys customer trust faster than a data breach.
They owe their customers a strict data protection policy when asking you to trust them with your personal information.
Here’s how they do it.
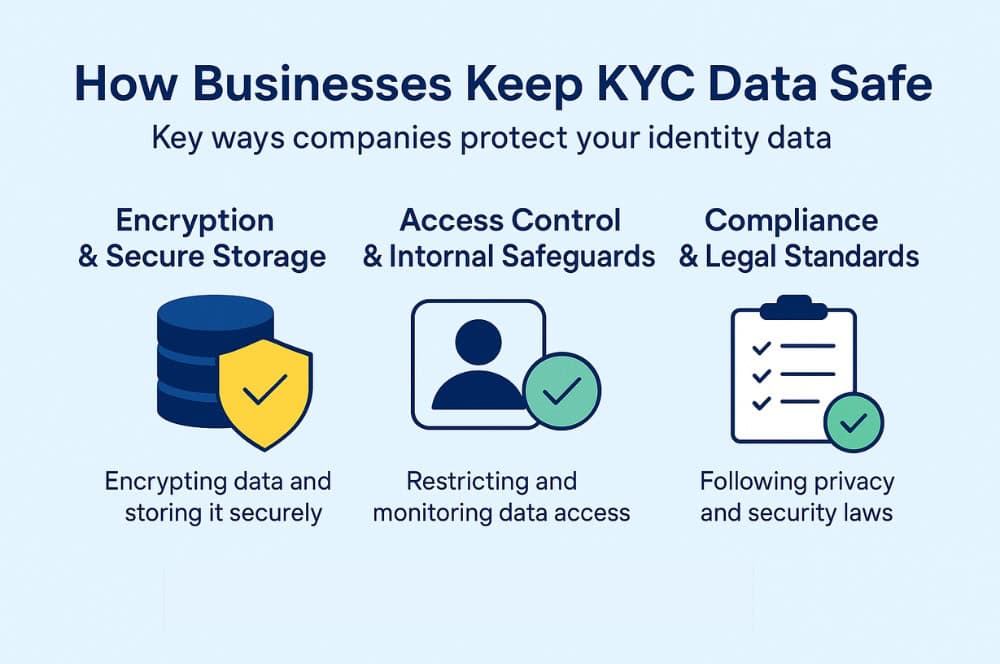
- Encryption and Secure Storage
Encryption refers to scrambling your information using strong cryptographic algorithms that can only be read by the company that asked for your data in the first place.
So, if a hacker cracks into their server, all they see is gibberish.
Data encryption occurs both at rest and in transit. It means that the databases and backups that store your data are encrypted.
Also, any time that data is transferred from one device to another, it travels through encrypted tunnels like TLS 1.2/1.3 that prevent any interception.
High-value data, like biometric info, is kept in separate storage spaces. The point of dividing data into different silos is to reduce the blast radius.
It ensures that if one storage area is compromised, the entirety of customer data doesn’t fall like dominoes.
- Access Control and Internal Safeguards
A surprising number of data incidents aren’t caused by hackers at all! They’re caused by people on the inside, either intentionally or by accident (simply because Gary from IT clicked a link he absolutely should not have)!
Businesses prevent such mishaps by restricting access to customer data.
Access control should be role-based, i.e., an employee only gets access to the chunk of the data that the nature of their job requires.
The process of logging into the database for access to data is also restricted by hardware keys and session limits. If the process doesn’t annoy employees at least a little, the security is probably too weak.
Businesses also have audit logs to watch the frequency and duration of data access an employee has.
In case someone starts downloading a suspicious amount of documents, higher authorities are notified.
- Compliance and Legal Standards
Businesses are required to protect KYC data because the law demands it.
GDPR or CCPA are privacy laws that dictate how customer data must be collected, stored, used, and deleted. If a business does not abide by the law, they are subject to massive fines.
Anti–money laundering (AML) laws require strict handling of all identity documents. Companies must prove not only that they performed KYC correctly but that they protected the data along the way.
Any reliable KYC verification software, like TruthScan, will always ensure compliance with these laws when handling customer data.
What You Can Do to Protect Your Information
Even though businesses carry most of the responsibility for keeping your KYC data safe, there are a handful of habits that reduce your exposure to data breaches.
- Never upload your ID documents over public Wi-Fi unless you want to gamble your identity for the price of a coffee. It is very easy to get around public networks and access the info shared through them.
- If you absolutely must use a shared connection, at least flip on a reputable VPN to encrypt your traffic.
- Always verify that the platform you upload your data to is legitimate. Check the domain, confirm the company’s real website directs you there, make sure the URL actually starts with HTTPS, and if you have the slightest bit of doubt, close the tab immediately.
- Keep your devices updated because outdated phones and laptops are prime targets for malware.
- Clean up after yourself. If you downloaded a PDF of your passport to upload somewhere, don’t leave it sitting in your “Downloads” folder for eternity. Delete it. Empty the trash as soon as possible.
- Lastly, make use of the user protection features of the platform being used for KYC verification. TruthScan has many such features that protect your data, such as:
- Two-factor authentication
- Encrypted uploads
- Secure, time-limited sessions
The Balance Between Verification and Privacy
KYC is a strange bargain.
On one hand, companies need to verify you’re a real person who isn’t laundering money on your lunch break. That verification demands personal details for them to abide by the laws and keep their licenses.
On the other hand, you’d prefer not to hand over your entire identity portfolio to any random business.
Smart companies will never try to collect every single bit of your very personal information. They will always look for the minimal set of documents that gets the job done.
To maintain the balance between your privacy and their verification needs, a responsible business will also explain where your data goes, how long it stays there, who gets to look at it, etc.
If someone’s making a digital clone of your passport, the least they can do is explain why.
The point is, privacy and verification can coexist if the system is built right.
The Future of Safe KYC
Currently, the KYC verification process is pretty fast and smooth. In the future, we aim to make it so safe that any one trying to intercept the system gets as little oxygen as possible.
Decentralized ID systems are not too far in the future. It means that you won’t have to hand over your documents every time a new platform wants to “verify” you.
You will hold a secure, cryptographically backed identity wallet and share only the tiny piece of info a service really needs.
In the future, we’ll also see blockchain-based verification, i.e., validating documents and credentials without storing those documents on any centralized database.
Zero-knowledge proof (ZKP) is a crypto method that lets you prove something is true without revealing the underlying information. It’s wild, but very real.
This tech, although currently in its early stages, has the potential to remove entire categories of sensitive data from the verification process altogether.
TruthScan is one of those tools built to adapt to these coming-of-age trends.
Το KYC verification architecture supports secure, encrypted uploads today, and it is made for decentralized credential flows tomorrow.
Τελικές σκέψεις
The world quite literally runs on identity verification. But as a customer, you should never hand over your information and simply hope it’s handled well.
Safety in KYC is the foundation of trust in every financial interaction you make.
And while no platform on Earth can promise 100% impenetrable protection (anyone who claims otherwise is selling you a fantasy), what can be guaranteed is responsibility.
TruthScan is built on that philosophy.
They are loud and clear about how seriously they treat your personal information by implementing every modern safety measure that exists today.
TruthScan is also ready to take on newer privacy-preserving technologies as they emerge.
Check out TruthScan for safe KYC verification today!
