Introduction: A New Era of AI-Driven Attacks
The year 2025 has marked a tipping point in cybersecurity. Generative AI has supercharged cyberattacks, enabling threat actors to launch more frequent, realistic, and scalable campaigns than ever before. In fact, over the past year an estimated 16% of reported cyber incidents involved attackers leveraging AI tools (e.g. image and language generation models) to enhance social engineering[1]. From ultra-convincing phishing emails to deepfake audio/video scams, malicious actors are weaponizing AI across all sectors. A majority of security professionals now attribute the surge in cyberattacks to generative AI, which gives bad actors faster, smarter ways to exploit victims[2]. Generative AI is effectively lowering the skill bar for cybercrime while increasing its potency.
Why is this so concerning? AI can instantly produce polished, context-aware content that fools even trained users. It can impersonate voices and faces with frightening accuracy, and even generate malicious code that morphs to evade detection. As a result, cyberattacks have become harder to detect and easier to execute. The World Economic Forum warns that 72% of organizations have seen increased cyber risks – especially social engineering and fraud – due to generative AI’s growing capabilities[3]. Real-world incidents bear this out: In early 2024, criminals used an AI-generated deepfake video call to impersonate a company’s CFO and trick an employee into transferring $25.6 million to the fraudsters[4]. And in another case, North Korean hackers used AI-generated fake ID documents to bypass security checks in a defense phishing campaign[5]. These examples highlight the stakes – generative AI is empowering scams that bypass both human and technical controls.
Yet AI is also part of the solution. Advanced detection tools (like those from TruthScan) use AI against AI – analyzing content for the subtle signatures of machine generation. In this whitepaper, we’ll examine the top AI-driven cyber threats of 2025 and how organizations can mitigate them. From AI-generated phishing to deepfake CEO fraud, AI-crafted malware, synthetic identities, and more, we’ll explore how generative AI is reshaping attacks. We’ll also discuss concrete defensive measures, including AI content detection, deepfake forensics, and identity verification technologies that can help security teams regain the upper hand. The goal is to illuminate how enterprises, MSSPs, CISOs, and fraud investigators can integrate AI detection tools across their cybersecurity stack to counter this wave of AI-powered threats.


Never Worry About AI Fraud Again. TruthScan Can Help You:
- Detect AI generated images, text, voice, and video.
- Avoid major AI driven fraud.
- Protect your most sensitive enterprise assets.
AI-Generated Phishing & BEC: Scams at Unprecedented Scale
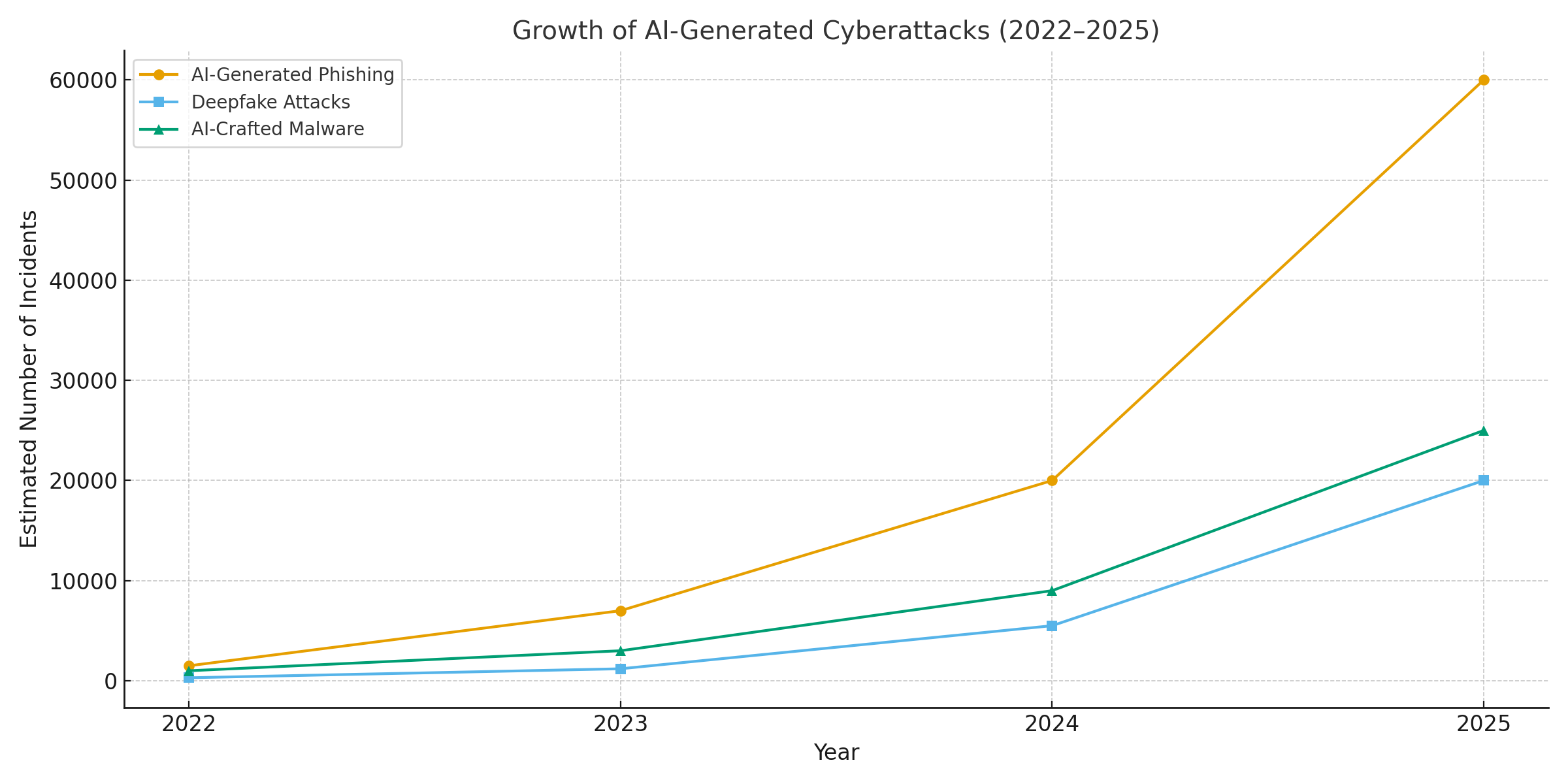
One of the clearest impacts of generative AI has been on phishing and business email compromise (BEC) schemes. AI-language models can draft fluent, contextually tailored emails in seconds – eliminating the tell-tale grammar mistakes and awkward phrasing that once gave phishing away. The result is a flood of highly convincing scam emails and texts. By April 2025, over half of spam emails (51%) were being written by AI, up from virtually zero two years prior[6]. Even more alarming, researchers found that about 14% of BEC attack emails were AI-generated by 2025[7] – a figure expected to climb as criminals adopt tools like ChatGPT. Some studies estimate over 80% of phishing emails may now have AI assistance in crafting them[8].
The volume of these AI-generated lures has exploded. Security analyses show phishing attacks linked to generative AI surged by 1,265% in a short span[9]. In one period, phishing incident reports jumped 466% in a single quarter, largely due to automated phishing kits and bots pumping out customized bait[9][10]. Why such a spike? Because AI lets attackers scale their operations dramatically. A single criminal can use an AI chatbot to generate thousands of personalized scam emails targeting different employees or customers, all in the time it used to take to craft one. This mass automation led the FBI to warn that BEC losses (which were already $2.7 billion in 2022) will only accelerate as AI “threatens to push those losses even higher”[11][12].
Not only are there more phishing emails, they’re also more effective. Victims are tricked at higher rates by the polished language and contextual details that AI can incorporate. In lab tests, AI-written phishing emails achieved a 54% click-through rate – far above the ~12% for traditional phishing attempts[13]. These messages read like a genuine CEO’s style or reference real company events, lowering recipients’ guard. Attackers even use AI to A/B test different phrasings and iterate on the most successful hooks[14]. And unlike humans, AI doesn’t make typos or get tired – it can spew endless variants until one slips past filters and fools someone.
Case in Point: In mid-2025, a Reuters investigation exposed how Southeast Asian scammers leveraged ChatGPT to automate fraud communications[15]. They generated convincing bank emails and customer service texts en masse, vastly increasing the reach of their schemes. European police similarly reported AI-driven phishing kits being sold on the dark web for under $20, enabling low-skilled actors to launch sophisticated campaigns[16][17]. The barrier to entry for BEC and phishing has essentially evaporated.
Defensive Measures – Stopping AI Phish: Given the onslaught, organizations must fortify their email and messaging channels. This is where AI content detection can help. Tools like TruthScan’s AI Text Detector and specialized email scanners can analyze incoming messages for the statistical markers of AI-generated text. For example, the TruthScan Email Scam Detector uses natural language analysis to flag emails that likely originated from an AI, even if they look legitimate[18]. These detectors examine things like perfectly polished grammar, sentence complexity, and stylometric patterns that are unusual for human writers. With real-time scanning, suspicious emails can be quarantined or flagged for review before they reach users. Enterprise security teams are beginning to deploy such AI-driven filters at email gateways and messaging platforms. In practice, this adds a new layer of defense on top of traditional spam filters – one explicitly tuned to catch AI-written content. As of 2025, leading enterprises are integrating solutions like TruthScan via API into their secure email gateways and cloud collaboration suites, creating an automated checkpoint for AI-generated phishing content.
Deepfake Voice & Video Impersonation: The “Seeing is Deceiving” Fraud
Perhaps the most visceral AI-driven threat in 2025 is the rise of deepfake voice and video attacks. Using AI models, criminals can clone a person’s voice from just a few seconds of audio, or generate a realistic video of someone’s face from a handful of photos. These deepfakes are being weaponized for high-stakes impersonation scams – from CEO fraud (“fake CEO” calls) to bogus video conferences and beyond. A recent industry report revealed 47% of organizations have experienced deepfake attacks of some kind[19]. And it’s not just theoretical: multiple heists in 2023–2025 have proven that deepfakes can defeat the ultimate authentication – our own eyes and ears.
One infamous case involved an international bank transfer of $25 million after an employee was deceived by a deepfake video conference. The attackers used AI to synthesize the likeness of the company’s CFO on a Zoom call, complete with her voice and mannerisms, instructing the employee to wire funds[4][20]. In another incident in Australia, a local government lost $2.3 million when scammers deepfaked both the voice and video of city officials to approve fraudulent payments[21]. And disturbingly, criminals are using AI-cloned voices in “grandparent scams” – calling seniors and impersonating their relatives in distress. The FBI and FinCEN issued alerts in late 2024 about a surge in fraud using AI-generated “deepfake” media, including fake customer service agents and synthetic identities to bypass KYC verifications[22].
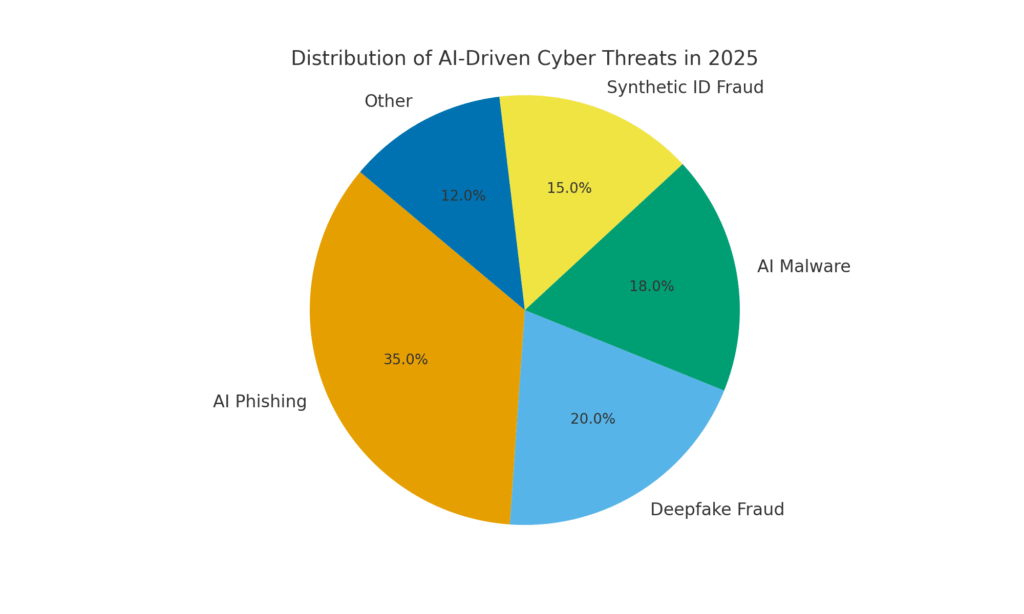
The frequency of deepfake-based crimes is climbing fast. By the end of 2024, one analysis showed a new deepfake scam was occurring every five minutes on average[23]. In Q1 2025 alone, reported deepfake incidents jumped 19% compared to all of 2024[24][25]. Deepfakes now account for an estimated 6.5% of all fraud attacks, a 2,137% increase since 2022[26][27]. The technology required has become easily accessible – often requiring as little as 30 seconds of audio to clone a voice, or under an hour of sample footage to model a person’s face convincingly[20]. In short, it’s never been easier to “fake” a trusted person’s identity and trick victims into handing over money or information.
Defensive Measures – Authenticating Reality: To counter deepfake threats, organizations are turning to advanced synthetic media detection tools. For example, TruthScan’s AI Voice Detector and TruthScan Deepfake Detector use AI to analyze audio and video for signs of manipulation. These systems perform frame-by-frame and waveform analysis to spot artifacts like unnatural facial movements, lip-sync issues, or audio spectral irregularities that betray an AI-generated clip. In tests, TruthScan’s algorithms achieved 99%+ accuracy in identifying AI-generated voices and detected manipulated video frames in real time[28][29]. In fact, researchers at Genians Security Center recently used TruthScan’s image forensics to analyze a fake ID card used by North Korean hackers – TruthScan’s deepfake image detector flagged the document as inauthentic with 98% confidence, foiling the spear-phishing attempt[5][30].
For practical defense, enterprises are deploying these detection capabilities at key choke points. Voice verification is being added to call center workflows – e.g. when a “client” requests a large transfer by phone, the audio can be run through a voice deepfake detector to ensure it’s really them (and not an AI mimic). Likewise, video conference platforms can integrate live deepfake scanning of participant video streams, to catch any synthetic faces. TruthScan’s deepfake detection suite, for instance, offers real-time video call analysis and facial authentication that can plug into Zoom or WebEx via API[31][29]. This means if someone tries to join a meeting using an AI-created video of your CEO, the system can flag “possible deepfake” before any damage is done. Additionally, important transactions now often include a verification step (out-of-band or multi-factor) that can leverage content authentication – e.g. requiring a brief spoken confirmation that is then checked by an AI voice detector for authenticity. By layering these tools, companies create a safety net: even if employees see or hear something plausible, a behind-the-scenes AI forensic will question its reality. In an AI-permeated threat landscape, “Don’t trust – verify” becomes the mantra for any voice or video communication involving money or sensitive access.
AI-Crafted Malware & Obfuscated Code: Evolving Threats in the Code
AI’s influence isn’t limited to social engineering – it’s also changing the game in malware development and evasive attack code. In 2025, Google’s Threat Intelligence Group uncovered the first malware strains using AI during execution to alter their behavior[32][33]. One example, dubbed PROMPTFLUX, was a malicious script that actually called out to an AI API (Google’s Gemini model) to rewrite its own code on the fly, producing new obfuscated variants to evade antivirus detection[34][35]. This “just-in-time” AI evolution marks a leap toward autonomous, polymorphic malware. Another sample, PROMPTSTEAL, used an AI coding assistant to generate one-line Windows commands for data theft, essentially outsourcing parts of its logic to an AI engine in real time[36][37]. These innovations point to a future where malware can continuously morph itself – much like a human pen-tester would – to defeat defenses.
Even without on-the-fly AI, attackers are using AI during development to create more potent malicious code. Generative AI can produce malware that is highly obfuscated, containing layers of confusing logic that hinder reverse engineering. According to threat intel reports, over 70% of major breaches in 2025 involved some form of polymorphic malware that changes its signature or behavior to avoid detection[38]. Additionally, 76% of phishing campaigns now employ polymorphic tactics like dynamic URLs or AI-rewritten payloads[38]. Tools like the dark-web offerings WormGPT and FraudGPT (unrestricted clones of ChatGPT) allow even non-experts to generate malware droppers, keyloggers, or ransomware code by simply describing what they want[39]. The result is an abundance of new malware variants. For example, in 2024 an info-stealer called BlackMamba emerged that was entirely AI-generated, using ChatGPT to write its code in segments – each execution produced a slightly different binary, confounding traditional signature-based antivirus[38]. Security researchers also demonstrated AI-generated polymorphic proof-of-concepts that could evade many endpoint protections[40].
On top of that, attackers are leveraging AI to fine-tune their delivery of malware. AI can intelligently script phishing emails (as discussed) that carry malware links. It can also help with exploit development – e.g. using AI to find new vulnerabilities or optimize shellcode. Nation-state actors have reportedly used advanced AI models to assist in discovering zero-day exploits and developing tailored malware for targets[41]. All these trends mean that malware in 2025 is stealthier and more adaptive. It’s often “co-created” with AI, making it harder to detect using conventional rules.
Defensive Measures – AI vs. AI in Malware Defense: Defending against AI-crafted malware requires a combination of advanced detection and AI-powered analysis on the defensive side. Many organizations are augmenting their endpoint protection and EDR (Endpoint Detection & Response) with AI/ML models that look for the behavioral patterns of AI-generated code. For instance, sudden on-host code transformations or unusual API call patterns might indicate something like PROMPTFLUX regenerating itself. Similarly, network monitoring can catch anomalies like malware reaching out to AI services (which is not “normal” for user applications). Vendors are training ML-based detectors on the families of AI-assisted malware identified so far, improving recognition of these novel threats.
One emerging solution is integrated AI content scanning in developer and build pipelines. This means using AI-driven detectors to analyze scripts, software builds, or even configuration changes for malicious or AI-generated content. For example, TruthScan’s Real-Time Detector can be deployed beyond just text – its multimodal analysis can potentially flag suspicious code or configuration files by recognizing if they were machine-generated with obfuscation patterns[42][43]. Development teams and MSSPs are starting to scan infrastructure-as-code scripts, PowerShell logs, and other artifacts for signs of AI-written segments that could indicate an attacker’s hand. While this is a nascent area, it shows promise: in one case, a security team used an AI detector to catch an obfuscated phishing kit file that “felt” AI-generated and indeed was part of an attack[44]. The file’s code was overly complex and verbose (hallmarks of AI generation), and an AI-content scan confirmed a high likelihood it wasn’t human-written[40].
Finally, threat intelligence sharing focused on AI threats is crucial. When Google GTIG publishes details of Prompt-based malware or when researchers report new AI-evasion techniques, organizations should feed those into their detection engineering. Behavioral analytics – looking for actions like a process spawning a script that rewrites that same process’s code – can catch anomalies that AI-assisted malware exhibits. In short, defenders must fight fire with fire: deploy AI-driven security tools that can adapt as quickly as the AI-driven malware does. This includes everything from AI-enhanced antivirus to user behavior analytics that can identify when an account or system starts acting “not quite human.” By embracing AI for defense, security teams can counter the speed and scale advantages that AI grants attackers.
Synthetic Identities and AI-Fueled Fraud Schemes
Moving from malware to the world of fraud: synthetic identity fraud has exploded with the help of generative AI. Synthetic identity fraud involves creating fictitious personas by combining real and fake data (e.g. real SSN + fake name and documents). These “Frankenstein” identities are then used to open bank accounts, apply for credit, or pass KYC checks – eventually resulting in unpaid loans or money laundering. It was already one of the fastest-growing fraud types, and AI has now poured fuel on the fire. Losses from synthetic ID fraud crossed $35 billion in 2023[45], and by early 2025 some estimates indicated nearly 25% of all bank fraud losses were due to synthetic identities[46]. Experian’s analysts found that over 80% of new account fraud in certain markets is now linked to synthetic IDs[19] – a staggering statistic underscoring how pervasive this scam has become.
Generative AI amplifies synthetic fraud in a few ways. Firstly, AI makes it trivial to produce the “breeder documents” and digital footprints needed to sell a fake identity. In the past, a fraudster might Photoshop an ID or manually create fake utility bills. Now, tools exist to generate authentic-looking profile photos, IDs, passports, bank statements, even social media profiles using AI image generators and language models[47][48]. For example, one can use an AI to create a realistic headshot of a person that doesn’t exist (preventing easy reverse-image searches), and generate a matching fake driver’s license with that photo. AI can also simulate “life signs” of an identity – e.g. creating records of synthetic parents, addresses, or social media posts to flesh out a backstory[49]. The Boston Fed noted that Gen AI can even produce deepfake audio and video of a fake person – for instance, a synthetic user could “appear” in a selfie verification video, complete with unique face and voice, all AI-generated[50].
Secondly, AI helps fraudsters scale up their operations. Instead of forging one or two identities at a time, they can programmatically generate hundreds or thousands of complete identity packages and auto-fill new account applications en masse[51][52]. Some dark web services are effectively offering “Synthetic Identities as a Service”, using automation to churn out verified accounts for sale. During the COVID-19 pandemic relief programs, for example, criminals used bots with AI-generated identities to apply en masse for loans and benefits, overwhelming the system with fake applicants. As Juniper Research projects, the global cost of digital identity fraud (fueled by these tactics) will rise 153% by 2030 compared to 2025[53].
Defensive Measures – Verifying Identity in an AI World: Traditional identity proofing methods are struggling against AI-created fakes. To adapt, organizations are adopting multi-layered identity and behavior verification bolstered by AI. A key layer is advanced document and image forensics. For instance, TruthScan’s AI Image Detector and Fake Document Detector provide the ability to analyze uploaded IDs, selfies, or documents for signs of synthesis or tampering. These tools examine pixel-level artifacts, lighting inconsistencies, and metadata to determine if an image is AI-generated or manipulated. They can catch subtle cues – like identical background patterns from GAN-generated photos, or fonts and spacing on an ID that don’t match any known government template. By deploying such detectors at onboarding, banks can automatically flag an applicant’s driver’s license or selfie if it’s likely AI-generated (for example, TruthScan’s system would have flagged the fake military ID used in the Kimsuky APT phishing case[5]). According to a TruthScan press release, their platform has been used by financial institutions to validate document authenticity at scale, identifying deepfakes with extremely high accuracy[54].
Another layer is behavioral analytics and cross-reference checks. Real identities have depth – years of history, public records, social media activity, etc. AI-generated identities, no matter how polished, often lack these deep roots. Banks and lenders now use AI to cross-correlate application data with public and proprietary data: Does this person’s phone number and email show a usage history? Does the device or IP geolocation make sense? Are they typing data in forms in a human way, or copy-pasting (as bots do)? AI models can be trained to distinguish genuine customer behavior from synthetic patterns. The Federal Reserve noted that “synthetic identities are shallow, and AI can see that” – AI-based verification can quickly search for the digital footprint of an identity and raise alarms if little to none is found[55]. In practice, identity verification services now employ AI that checks if a user’s selfie matches past photos (to detect face swaps) and even prompts users with randomized actions (like specific poses or phrases) during liveness checks, making it harder for deepfakes to respond correctly[56][57].
Finally, continuous monitoring of account behavior post-onboarding helps catch synthetic accounts that slipped through. Since these accounts aren’t tied to a real persona, their usage patterns often eventually stand out (e.g. making perfectly timed transactions to build credit, then maxing out). AI-driven fraud monitoring (such as Sift’s or Feedzai’s platforms) can identify anomalies in how accounts are used, flagging potential synthetics for review. In summary, fighting AI-enabled identity fraud requires AI-enabled identity proofing – combining document forensics, biometric checks, data correlation, and behavioral analysis. The good news is that the same AI advancements enabling the fraud are also being used to detect it. TruthScan, for example, offers an identity verification suite that integrates text, image, and voice analysis to vet new users. By leveraging these tools, one large bank noted a significant drop in successful synthetic account openings, even as industry averages were rising. The arms race continues, but defenders are learning to spot the faint “digital tells” of a synthetic, no matter how well AI tries to cover its tracks.
Integrating AI Detection Across the Security Stack
We’ve explored several distinct threat areas – phishing, deepfakes, malware, synthetic fraud – all supercharged by AI. It’s clear that no single tool or one-time fix will solve the challenge. Instead, enterprises need a comprehensive strategy to embed AI-powered detection and verification at every layer of their cybersecurity stack. The approach must mirror the attack surface, covering email, web, voice, documents, identity, and beyond. The diagram below illustrates how organizations can integrate TruthScan’s AI detection tools (and similar solutions) across common enterprise security layers:
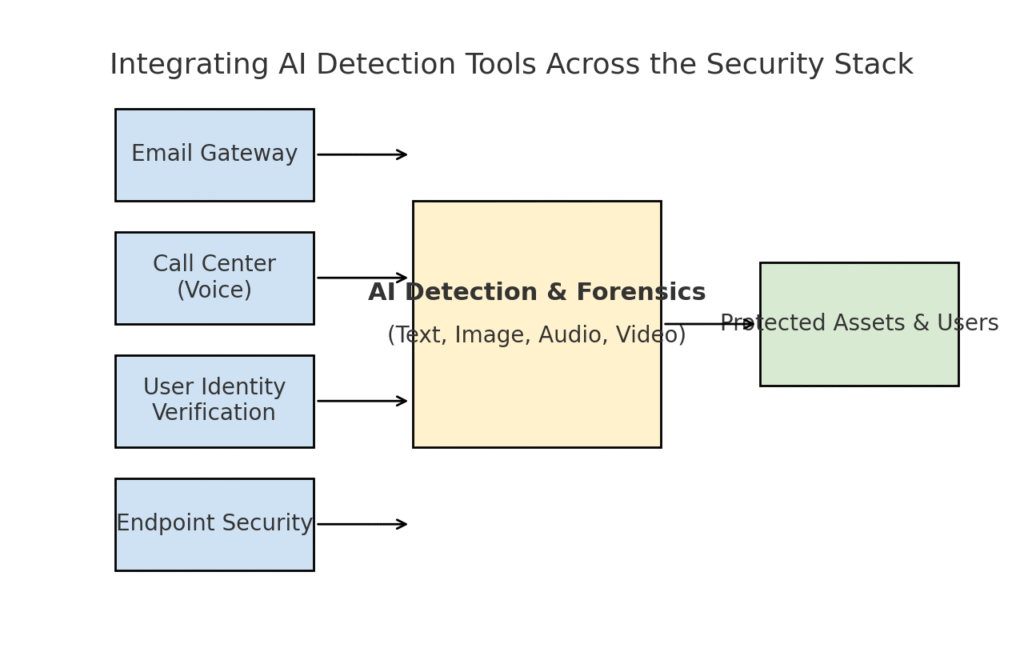
Integrating AI detection tools at multiple layers of the security stack – from email gateways and call centers to user verification and endpoint protection. AI content detection (center) analyzes text, images, audio, and video in real time, feeding into enforcement points that protect assets and users.
In this model, multi-modal AI detectors act as a central brain that interfaces with various security controls:
- Email Gateways: Inbound emails pass through an AI text/scam detector before reaching the inbox. This ties into the phishing defense we discussed – e.g. using TruthScan’s Email Scam Detector via API at your email provider to automatically quarantine suspicious AI-generated emails[18]. It can also be applied to messaging platforms (chat apps, SMS gateways) to scan content for phishing or scam patterns.
- Call Centers and Voice Systems: Telephone and VOIP channels are secured by integrating voice deepfake detection. For instance, a bank’s customer support line could use TruthScan’s AI Voice Detector to analyze incoming caller audio in real time and alert if a caller’s voiceprint is synthetic or doesn’t match their known profile[58][59]. This helps prevent vishing and voice impersonation attacks (like fake CEO calls) from succeeding.
- User Identity Verification Processes: During account creation or high-risk user actions (password resets, wire transfers), AI-driven identity verification kicks in. An uploaded photo ID is vetted by an image forensics tool (e.g. checking if it’s AI-generated or a photo of a photo), and a selfie or video call is screened by a deepfake detector. TruthScan’s Deepfake Detector can be utilized here to perform facial authentication – ensuring the person on camera is real and matches the ID[60][61]. Behavioral signals (typing cadence, device consistency) can also be fed into AI models to detect bots or synthetic identities.
- Endpoints and Network: Endpoint security agents and proxy servers can incorporate AI content analysis for files and scripts. For example, if an endpoint EDR sees a new script or EXE executing, it could send the file’s text content to an AI detector to check if it resembles known AI-generated malware or exhibits traits of obfuscated AI code. Similarly, DLP (data loss prevention) systems might use AI text detection to flag sensitive text that was AI-generated (which could indicate an insider using AI to draft data exfiltration messages or falsify reports). TruthScan’s Real-Time Detector is designed to plug into such workflows, offering live analysis of content across platforms with automated response options[42][62] (for instance, auto-blocking a file or message if it’s identified as AI-generated malware or disinformation).
The key benefit of this integrated approach is speed and consistency. AI attacks move quickly – phishing emails, fake voices, and synthetic data can hit many channels at once. By instrumenting all those channels with AI detection, an organization gains real-time visibility and defense-in-depth. One team described it as creating an “AI immune system” for their enterprise: whenever something is communicated (be it an email, a document upload, a voice call, etc.), the AI immune system “sniffs” it for foreign (AI-generated) signatures and neutralizes it if found malicious.
TruthScan’s enterprise suite exemplifies this, as it offers a unified platform covering text, image, audio, and video AI detection that can be deployed modularly or as a whole[63][64]. Many companies start by deploying one or two capabilities (say, text detection in email and image detection in onboarding) and then expand to others once they see the value. Importantly, integration is made developer-friendly – TruthScan and similar services provide APIs and SDKs so that security teams can hook detection into existing systems without massive re-engineering. Whether it’s a SIEM, an email gateway, a custom banking app, or a CRM system, the detection can run behind the scenes and feed alerts or automated actions. For example, a large social media platform integrated content moderation APIs to automatically takedown deepfake videos within minutes of upload[65][66], preventing the spread of AI-generated misinformation.
Conclusion: Staying Ahead of the Curve
The rapid proliferation of AI-driven threats in 2025 has challenged organizations in new ways. Attackers have found means to exploit human trust at scale – impersonating voices and identities, automating social engineering, evading defenses through adaptive code, and fabricating entire false realities. It’s a daunting prospect for defenders, but not a hopeless one. Just as criminals are harnessing AI, so too can we enlist AI on the side of security. The emergence of AI content detection, deepfake forensics, and synthetic identity scanners gives us powerful counters to these new threats. By deploying these tools and integrating them across all layers of defense, enterprises can dramatically reduce the risk of AI-powered attacks slipping through. Early adopters have already thwarted multi-million dollar fraud attempts by catching deepfakes in the act[26], or prevented phishing disasters by filtering out AI-crafted emails.
Beyond technology, organizations should cultivate a culture of “trust but verify.” Employees should be aware that in the era of AI, seeing (or hearing) isn’t always believing – a healthy skepticism paired with verification workflows can stop many social engineering ploys. Training and awareness, combined with automated verification tools like TruthScan, form a formidable defense. In a sense, we must raise the bar for authentication and validation of information. Digital communications and documents can no longer be taken at face value; their provenance needs to be checked, either by machine or by process.
As we move forward, expect attackers to further refine their AI tactics – but also expect continued innovation in defensive AI. The cat-and-mouse dynamic will persist. Success for defenders will hinge on agility and intelligence sharing. Those who rapidly incorporate new threat intelligence (e.g. novel deepfake detection techniques or updated AI model signatures) will stay ahead of attackers leveraging the latest AI tools. Collaborations between industry, academia, and government will also be vital in this fight, as seen by the alerts and frameworks emerging from agencies like NIST’s AI Risk Management Framework and inter-bank collaborations on fraud AI detection.
In closing, the cybersecurity industry is in the midst of an AI-driven paradigm shift. The threats are unlike those of a decade ago, but we are meeting them with equally unprecedented defenses. With a combination of advanced detection technology and robust security strategy, we can mitigate the risks of generative AI and even turn it to our advantage. Tools like TruthScan’s AI detection suite enable us to restore trust in a zero-trust world – to ensure that the person on the other end of the line is real, that the document in our inbox is authentic, and that the code running in our network hasn’t been tampered with by a malicious AI. By investing in these capabilities now, organizations will not only protect themselves from today’s AI-enabled attacks but also build resilience against the evolving threats of tomorrow. The takeaway is clear: AI may be supercharging cyberattacks, but with the right approach, it can also supercharge our defenses.
Sources: Relevant data and examples have been drawn from 2025 threat intelligence reports and experts, including Mayer Brown’s Cyber Incident Trends[1][67], Fortinet’s 2025 threat roundup[2][19], Barracuda research on AI email attacks[6][7], Google GTIG’s AI threat report[34], Boston Federal Reserve insights on synthetic fraud[45][50], and TruthScan’s published case studies and press releases[30][26], among others. These illustrate the scope of AI-driven threats and the efficacy of AI-focused countermeasures in real-world scenarios. By learning from such intelligence and deploying cutting-edge tools, we can navigate the age of AI-enhanced cyber risk with confidence.
[1] [67] 2025 Cyber Incident Trends What Your Business Needs to Know | Insights | Mayer Brown
[2] [3] [19] Top Cybersecurity Statistics: Facts, Stats and Breaches for 2025
https://www.fortinet.com/resources/cyberglossary/cybersecurity-statistics
[4] [11] [12] [16] [17] [20] [22] [47] [48] [52] AI-Driven Fraud in Financial Services: Recent Trends and Solutions | TruthScan
https://truthscan.com/blog/ai-driven-fraud-in-financial-services-recent-trends-and-solutions
[5] [26] [30] [54] TruthScan Detects North Korean Deepfake Attack on Defense Officials – Bryan County Magazine
[6] [7] [14] Half the spam in your inbox is generated by AI – its use in advanced attacks is at an earlier stage | Barracuda Networks Blog
https://blog.barracuda.com/2025/06/18/half-spam-inbox-ai-generated
[8] [10] Q2 2025 Digital Trust Index: AI Fraud Data and Insights | Sift
https://sift.com/index-reports-ai-fraud-q2-2025
[9] [13] [24] [25] [38] [39] AI Cybersecurity Threats 2025: $25.6M Deepfake
https://deepstrike.io/blog/ai-cybersecurity-threats-2025
[15] [21] Latest Threat Intelligence | TruthScan
[18] [63] [64] TruthScan – Enterprise AI Detection & Content Security
[23] [46] [56] [57] Deepfakes and Deposits: How to Fight Generative AI Fraud
https://www.amount.com/blog/deepfakes-and-deposits-how-to-fight-generative-ai-fraud
[27] Deepfake Attacks & AI-Generated Phishing: 2025 Statistics
https://zerothreat.ai/blog/deepfake-and-ai-phishing-statistics
[28] [58] [59] AI Voice Detector for Deepfakes & Voice Cloning | TruthScan
https://truthscan.com/ai-voice-detector
[29] [31] [60] [61] [65] [66] Deepfake Detector – Identify Fake & AI Videos – TruthScan
https://truthscan.com/deepfake-detector
[32] [33] [34] [35] [36] [37] [41] GTIG AI Threat Tracker: Advances in Threat Actor Usage of AI Tools | Google Cloud Blog
https://cloud.google.com/blog/topics/threat-intelligence/threat-actor-usage-of-ai-tools
[40] Hackers Obfuscated Malware With Verbose AI Code
https://www.bankinfosecurity.com/hackers-obfuscated-malware-verbose-ai-code-a-29541
[42] [43] [62] Real-time AI Detection – TruthScan
https://truthscan.com/real-time-ai-detector
[44] EvilAI Operators Use AI-Generated Code and Fake Apps for Far …
https://www.trendmicro.com/en_us/research/25/i/evilai.html
[45] [49] [50] [51] [55] Gen AI is ramping up the threat of synthetic identity fraud – Federal Reserve Bank of Boston
[53] Synthetic Identity Fraud 2025: AI Detection & Prevention Strategies